In the vast expanse of the digital cosmos, data security stands as a beacon of utmost importance. Each day, an astronomical volume of sensitive data zips through the cybernetic realm, where digital predators lie in wait. The risks tied to sharing such valuable information can be dire—ranging from identity theft to corporate espionage. In response, this blog post illuminates the pathway to safeguarding our digital treasures through Managed File Transfer (MFT), a solution engineered for the secure and swift sharing of data. Embark on this journey with us to fortify your digital defenses with MFT.
Understanding Managed File Transfer (MFT)
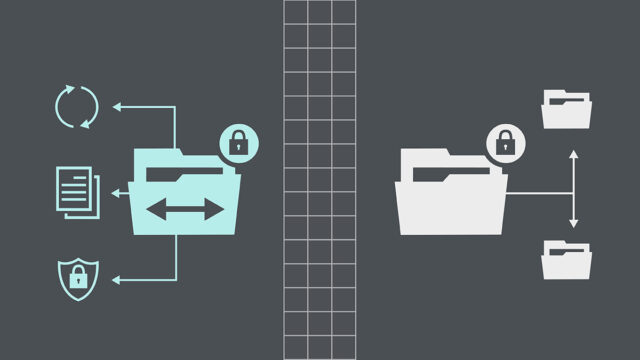
Managed File Transfer is akin to a fortified courier of the digital age, entrusted with the secure transit of sensitive information. Distinct from the rudimentary methods of yesteryear, MFT melds advanced security, management, and audit capabilities to safeguard file transfers against the vulnerabilities that plague traditional systems. Where simple file transfer protocols falter, MFT stands resilient, bolstering the protection of data with layers of security and ensuring it reaches its destination untainted and unbreached.

The Need for Swift Data Sharing
The modern business landscape is a race against time where the swift sharing of data can mean the difference between a missed opportunity and a market conquest. In sectors like healthcare, finance, and logistics, the velocity of data exchange is not just a convenience but a critical component of operations. As businesses pivot towards real-time analytics and instant decision-making, the requirement for rapid and reliable information sharing becomes unequivocal—a digital imperative that underpins the need for sophisticated transfer solutions.
Challenges in Traditional File Transfer
The traditional methods of file transfer are beleaguered with limitations. Vulnerable to interceptions, they expose sensitive information to significant security risks. Furthermore, they often lack the efficiency to cope with the colossal size and complex formats of modern data. This insufficiency hinders the ability to maintain the sanctity of sensitive information, rendering these antiquated methods obsolete for contemporary needs where protecting information is not just an option but a necessity.
Benefits of Managed File Transfer
Implementing Managed File Transfer solutions unfolds a plethora of advantages. Security is heightened through end-to-end encryption, thwarting unauthorized access. Automation streamlines workflows, eliminating human error, and ensuring consistent transfer protocols. MFT also offers robust compliance features, aligning with legal and regulatory frameworks—key advantages that traditional file transfer systems lack, thus ensuring that data sharing is both secure and efficient.

Key Features of a Reliable MFT Solution
A reliable MFT solution is furnished with a suite of pivotal features. Encryption fortifies data against unauthorized access, while user access control ensures that only vetted individuals handle sensitive files. Audit trails offer a meticulous record of file transfer activity, essential for compliance and security analysis. Furthermore, scalability allows the system to adapt to the growing information demands of a business, ensuring longevity and flexibility of the data transfer infrastructure.
Ensuring Data Privacy and Compliance
MFT stands as a bulwark in maintaining data privacy and meeting stringent compliance demands. With regulations like GDPR and HIPAA setting the bar for data protection, MFT systems are designed to navigate the complex lattice of legal requirements. They enable organizations to uphold the highest standards of information privacy, fortifying against breaches and penalties, and fostering trust in an era where data is both currency and commodity.
MFT Implementation Best Practices
The deployment of an MFT solution is not without its intricacies. Best practices suggest a structured approach, emphasizing user training to foster adeptness in handling the system. Comprehensive training modules tailored to different roles can significantly enhance the efficiency and security of operations. Ongoing monitoring is crucial, ensuring that any anomalies are swiftly detected and addressed. Regularly updated protocols are recommended to adapt to new threats. This strategic implementation fortifies the information transfer process against evolving threats and harnesses the full potential of MFT technology, ensuring a robust defense for sensitive information. Including stakeholders in planning can also ensure that the solution meets diverse needs.

Case Studies: Real-World MFT Success Stories
The business annals are rich with MFT success stories. Companies, big and small, have reaped the benefits of secure data transfer systems. These narratives often share a common theme—significant improvements in data handling efficiency and security. From healthcare institutions safeguarding patient records against breaches to financial firms protecting transaction information against cyber theft, MFT solutions have not only met but exceeded the rigorous demands of secure data sharing, validating their efficacy and indispensability. Many have seen a reduction in operational costs due to the elimination of manual processes, adding to the ROI of the MFT solution.
Choosing the Right MFT Solution
Selecting the appropriate MFT solution requires a careful balancing act, weighing factors such as scalability, integration capabilities, and cost. A thorough evaluation should consider the specific data sharing needs of the organization and how well the solution can integrate into the existing IT infrastructure, without disrupting current workflows. Cost must also be considered, ensuring that the investment in an MFT solution delivers on its promise of security and efficiency without causing financial strain. Moreover, it’s essential to ensure that the solution can grow with the company, avoiding future obsolescence.
Tips for Secure Data Sharing
For individuals leveraging MFT solutions, certain practices enhance security. Robust password management is imperative—complex passwords deter unauthorized access and regular changes to these passwords can significantly increase security. File encryption adds an extra layer of security, ensuring that information remains protected both at rest and in transit. Additionally, educating users on the importance of not sharing sensitive information outside the MFT system can prevent accidental breaches. By adhering to these tips, users can significantly mitigate the risks associated with data sharing, leveraging the strengths of MFT to maintain the confidentiality and integrity of their information.

Conclusion
This exploration underscores the pivotal role of Managed File Transfer in the contemporary data-sharing landscape. By adopting MFT, organizations can ensure swift, secure data transfer, an essential facet of modern business operations. As we conclude, let us emphasize the imperative to act—to safeguard our information with the diligence it demands. The adoption of MFT is not just a strategic move but a foundational one in the quest for digital security and operational efficiency.